Chinese hackers connection still active in Indian computer systems, US firm said
 |
| Representative image. | Pixabay |
Stuart Solomon, the firm’s chief operating officer said they could see a ‘handshake’ – which is an indication of an exchange of traffic – between a China-linked group and an Indian maritime port. Calling the group ‘Red Echo’, the firm said it had targeted as many as 10 entities under India’s power grid as well as two maritime ports when Recorded Future first notified India’s Computer Emergency Response Team on February 10. Solomon said most of these connections were still operational as recently as February 28.
“There’s still an active connection between the attacker and the attackee. It’s still happening,” Solomon told Bloomberg, referring to the port.
Chinese Foreign Ministry spokesman Wang Wenbin said without any proof, slandering a specific side was “irresponsible behavior and an ill-intentioned one”.
The cyber-attack attempt assumes significance as it comes at a time when a US newspaper reported recently that the 2020 power blackout in Mumbai was due to a China-based cyber-attack. Computer networks of at least 12 Indian state-run organisations, primarily power utilities and load dispatch centres, have been targeted by Chinese state-sponsored groups since mid-2020 in an attempt to inject malware that could cause widespread disruptions, the study by Recorded Future had revealed.
According to the US-based company that monitors the use of the internet by state actors for cyber-campaigns, NTPC Limited, the country’s largest power conglomerate; five primary regional load dispatch centres that aid in the management of the national power grid by balancing electricity supply and demand; and two ports were among the organisations attacked.
The activity appears to have started well before the May 2020 clashes between Indian and Chinese troops that triggered the border standoff along the Line of Actual Control in eastern Ladakh, the report said. It further stated, there was a “steep rise” in the use of a particular software by Chinese organisations to target “a large swathe of India’s power sector” from the middle of last year.
Recorded Future has not made any connection between the traffic observed under RedEcho and the Mumbai outage. “It’s not unusual to see this type of technique used by nation states as an instrument of national power,” Solomon, however, said.
He added that this could be “as simple as trying to drive influence operations to be able to signal either to the people or the government that at any given time they have leverage that can be used against them.”
According to Solomon, the 10 entities RedEcho infiltrated account for “nearly 80% of India’s land mass from an electricity-coverage perspective” and could have remained unexposed and undetected until they were “needed as leverage”. He said if it was “meant to take down the lights, it would have taken down the lights, but it did not.”
RedEcho and how we know it’s linked to China
Recorded Future linked the group of hackers, which it nicknamed RedEcho, to China because it used infrastructure connected to the malware ‘ShadowPad’, attributed to other Chinese hacker groups.
Since early 2020, the firm said, it observed a “large increase in suspected targeted intrusion activity against Indian organizations from Chinese state-sponsored groups”.
“Mid-2020 onwards”, the firm noted, “a steep rise in the use of infrastructure” linked to ShadowPad malware “to target a large swathe of India’s power sector”.
 |
| Representational image | Photographer: Chris Ratcliffe | Bloomberg |
The ShadowPad link
ShadowPad was discovered in 2017. The malware had been injected into software updates provided by a legitimate software provider, NetSarang, that is headquartered in the US and South Korea.
According to cybersecurity and antivirus provider Kaspersky, NetSarang was not aware that its supply chain had been compromised and its software updates were carrying the malicious code.
The ShadowPad malware steals data from a ‘victim’ computer and is able to automatically communicate with the computer servers at the hacker’s end. Once every eight hours, ShadowPad sends back information like user name, domain name, host name to the hacker’s computer system.
When an “interesting” target is found, the hacker’s computer server can seek more information from the victim system via the malware and even deploy more malicious code.
The 2017 ShadowPad hack was attributed to ‘APT41’, the Recorded Future report said.
APT41 is a prolific cyber threat group that carries out “Chinese state-sponsored espionage activity” apart from financially motivated activity “potentially outside of state control”, according to cybersecurity firm FireEye.
Since 2012, the group has targeted organisations in at least 14 countries and is known to steal intellectual property.
“Presently, we are aware of at least 5 Chinese threat activity groups using ShadowPad, including APT41, Tonto Team, groups using the Icefog malware, KeyBoy, and Tick”, the study noted.
“We assess that the sharing of ShadowPad is prevalent across groups affiliated with both Chinese Ministry of State Security (MSS) and groups affiliated with the People’s Liberation Army (PLA)”, the study adds.
RedEcho shadow on critical Indian sectors
Recorded Future did not specify exactly how the hackers would have accessed India’s critical sector, according to Yash Kadakia, chief technology officer of Mumbai-based cybersecurity firm Security Brigade InfoSec.
Kadakia, who went through the study, said: “It is difficult for a private, outside entity to confirm how or what the attackers access on victim computers without the government allowing the company to access those targeted computer systems.”
According to its report, the US cybersecurity firm had identified that an internet address of an Indian critical sector organisation was potentially sending data back to an internet domain set up by RedEcho. The study detected that on 30 December 2020, “at least 1.29 MB” of data was sent back to an internet address linked to RedEcho from a victim’s internet address.
However, the 1 March power ministry statement refutes this. It stated that “no communication & data transfer” to internet addresses linked to RedEcho had taken place.
According to Recorded Future, among the list of “suspected victim organizations” are the Power System Operation Corporation Limited (POSOCO), regional-level electricity Load Despatch Centres for West, South, Northeastern and Eastern parts of the country, state-level electricity load despatch centres for Telangana and Delhi, and the Mumbai Port Trust.
India-China tensions
![Indian Border Security Force (BSF) soldiers guard a highway leading towards Leh, bordering China, in Gagangir [Tauseef Mustafa/AFP] 4218-468e80f1b247479a8ef7670e4d89494b-18](https://vietnamtimes.org.vn/stores/news_dataimages/minhchauvnt/032021/04/09/4218_468e80f1b247479a8ef7670e4d89494b_18.png?rt=20210304110325) |
| Indian Border Security Force (BSF) soldiers guard a highway leading towards Leh, bordering China, in Gagangir [Tauseef Mustafa/AFP] |
Border tensions flared up in June after deadly clashes between Indian and Chinese soldiers in Ladakh’s Galwan Valley. Twenty Indian soldiers were killed in the clashes. China identified the casualties on its side only in February, saying that four soldiers died.
The talks between the militaries of the two countries began soon after the clashes. However, a breakthrough came only in February as Union Defence Minister Rajnath Singh informed the Parliament about the disengagement agreement reached between India and China.
The disengagement process along Pangong Tso in Ladakh began on February 10, as military commanders began pulling out troops, tanks and artillery from the area in the first step towards full withdrawal. The process has been completed. On February 20, India and China held commander-level talks to discuss pulling back from other areas.
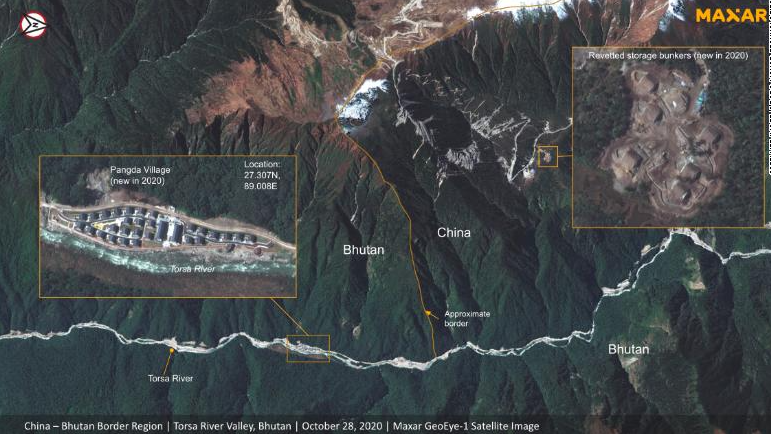 | China allegedly developing area along disputed border with India and Bhutan New satellite images appear to show China has built up an area in the Himalayas along a disputed border with India and Bhutan that was ... |
 | India hands over missing Chinese soldier The Chinese soldier who strayed across the Line of Actual Control (LAC) in Demchok sector on October 18 has been returned, both India and China ... |
 | Captured Chinese soldier by India along disputed mountain border, updates The Indian military revealed on Monday that its forces had captured a Chinese corporal who had strayed across the disputed, unmarked high-altitude border that zigzags ... |
 World
World
China’s Bid to ‘Change Status Quo’ on LAC Thwarted, says Indian Defence Minister Rajnath Singh
 World
World
Enough Room in World for China, India; Let's Not Interfere in Other's Affairs, Says Outgoing Envoy
Recommended
 World
World
India reports 9 Pakistani Aircraft Destroyed In Operation Sindoor Strikes
 World
World
Thailand Positions Itself As a Global Wellness Destination
 World
World
Indonesia Accelerates Procedures to Join OECD
 World
World
South Korea elects Lee Jae-myung president
 World
World
22nd Shangri-La Dialogue: Japan, Philippines boost defence cooperation
 World
World
Pakistan NCRC report explores emerging child rights issues
 World
World
"India has right to defend herself against terror," says German Foreign Minister, endorses Op Sindoor
 World
World





