Maze Ransomware: Who is the most notorious cybercrime gang going to "disband"
How can Maze Ransomware infect your devices?
According to Bleeping Computer, the Maze ransomware began operating in May 2019 but became more active in November. That's when the media-savvy operation revolutionized ransomware attacks by introducing a double-extortion tactic.
While ransomware operations have always enjoyed taunting news sites and researchers, for the most part, they tended to ignore journalists' emails.
This changed in November 2019, when Maze contacted BleepingComputer to let us know that they stole the unencrypted data for Allied Universal before encrypting them.
Maze stated that if Allied didn't pay a ransom, their data would be publicly released. Ultimately, the ransom was not paid, and Maze released the stolen data.
 |
| Photo: Bank Info Security |
Soon after, Maze launched a 'Maze News' site that they use to publish non-paying victims' data and issue "press releases" for journalists who follow their activities.
This double-extortion technique was quickly adopted by other large ransomware operations, including REvil, Clop, DoppelPaymer, who released their own data leak sites. This double-extortion technique has now become a standard tactic used by almost all ransomware operations.
According to Heimdal Security, the criminals initially distributed the ransomware via spam e-mail and exploit kits, but now they use a variety of tactics, techniques and procedures. They might even hire actors to analyse their next victim’s organisation and determine its annual revenue. The e-mails they were sending had “Missed package delivery” and “Your AT&T wireless bill is ready to view” at the subject line and were sent using several malicious domains with the registrant address abusereceive@hitler.rocks.
Once the maze operators find a gap in a network, their next step is to obtain elevated privileges, conduct lateral movement and then begin to deploy file encryption across all drives, not before exfiltrating the data they discover. The data is encrypted using the ChaCha20 and RSA algorithms.
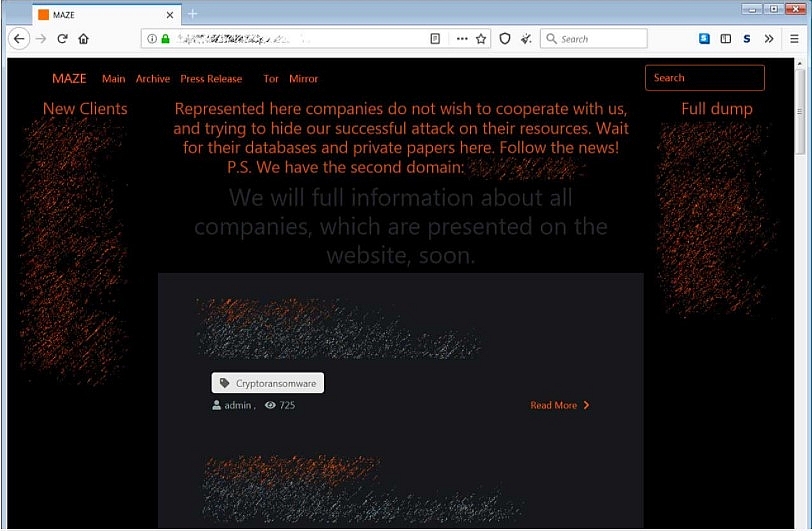 |
| Maze data leak site. Photo: Bleeping computer. |
Maze continued to evolve ransomware operations by forming a ransomware cartel with Ragnar Locker and LockBit, to share information and tactics.
During their year and a half cybercrime spree, Maze has been responsible for attacks on notable victims, including Southwire, City of Pensacola, Canon, LG Electronics, Xerox, and many more.
Declaring retirement notice but casting doubt on switching over to a new ransomeware operation
According to Bank Info Security, Maze posted a "retirement" notice to its darknet site on Nov. 1 saying: "This project is now closed." The word "project" appears to be a reference to the ransomware gang stating in the note that its attacks were intended to teach its victims the danger of having poor security practices. The gang also denied it was ever the center of a larger group. The note ended with the group saying it would be back.
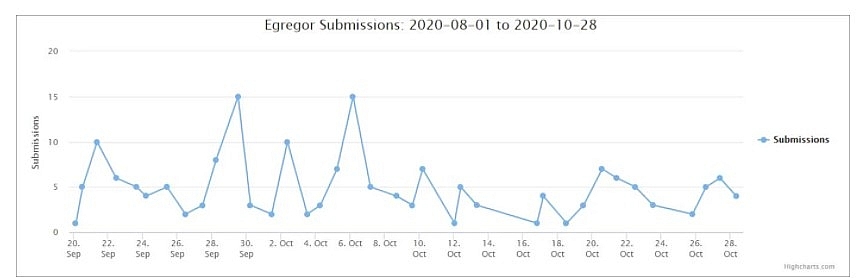 |
| Egregor submissions graph to ID-Ransomware. Photo: Bleeping computer. |
The consensus from cybersecurity executives is that Maze has closed up shop with activity on its site having decreased and no new attacks recently spotted. But it is noted that cybercriminals are not honest individuals, meaning any halt may be brief.
BleepingComputer has learned that many Maze affiliates have switched over to a new ransomware operation called Egregor.
Egregor began operating in the middle of September, just as Maze started shutting down their encryption operation. It quickly became very active, as seen by the ID-Ransomware submission graph below.
Egregor is believed to be the same underlying software as both Maze and Sekhmet as they utilize the same ransom notes, similar payment site naming, and share much of the same code.
This was also confirmed by a ransomware threat actor who stated that Maze, Sekhmet, and Egregor were the same software.
 |
| Photo: IT Pro. |
Ransomware expert Michael Gillespie, who analyzed both Egregor and Sekhmet, also found that Egregor victims who paid a ransom were sent decryptors that were titled 'Sekhmet Decryptor.'
Unfortunately, this shows that even when a ransomware operation shuts down, it does not mean the threat actors involved retire as well. They just move to the next ransomware operation.
What do experts say about the Maze's retirement notice?
"Ransom actors are professional liars and scammers; to believe anything they say is a mistake. Maze as we know it might be shutting down, but the actors behind it feel like they've got some kind of 'holy mission' to expose the weaknesses of corporate networks, for-profit, so I doubt we'll see them gone forever," says Adam Kujawa, director of Malwarebytes Labs.
Jamie Hart, cyber threat intelligence analyst at Digital Shadows, notes that while the group did clean up its data leak site - Maze News - during October by posting the full dumps for victims, the gang has not encrypted any new victims during the past 30 days or so. The announcement, however, did leave the door open for its return.
"The press release stated that the group would be back, so the Maze threat is likely not finished," Hart says.
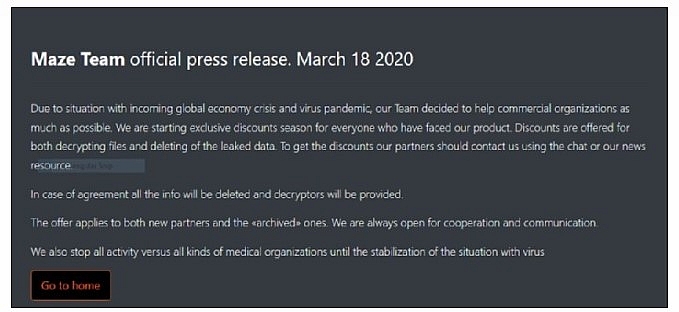 |
| Photo: Computer Weekly.com |
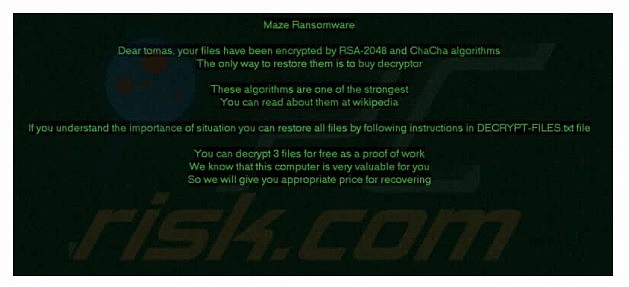 |
| Photo: PC Risk.com |
Even if Maze has decided to cease operating, the move will have no real impact on the threat landscape, Brett Callow, a threat analyst with Emsisoft says.
"Their affiliates will join other groups or simply start their own operations. Unfortunately, ransomware is far too profitable for the retirement of any one group to have any significant effect," Callow says.
The group likely decided to halt its operations because of the amount of attention it has been receiving, especially since its antics, such as creating data leak sites for their victims, have influenced the operations of ransomware groups across the world, Kujawa says.
 | Vietnam respects human rights in cyberspace The Vietnamese Party and State pay attention to ensuring people’s right to access information because it’s a fundamental human right. |
 | Cyber attack on Australian Government may be China's revenge for banning Huawei Ex-officials have claimed that a cyber attack suspected to have been carried out by China against Australia could have been a revenge for the banning ... |
 | Vietnam’s information systems hit by nearly 1,500 cyber attacks Vietnam's information system has been witnessing a decrease in cyber-attacks lately, with nearly 1500 attacks in the first five months of 2020. |
Recommended
 World
World
India reports 9 Pakistani Aircraft Destroyed In Operation Sindoor Strikes
 World
World
Thailand Positions Itself As a Global Wellness Destination
 World
World
Indonesia Accelerates Procedures to Join OECD
 World
World
South Korea elects Lee Jae-myung president
 World
World
22nd Shangri-La Dialogue: Japan, Philippines boost defence cooperation
 World
World
Pakistan NCRC report explores emerging child rights issues
 World
World
"India has right to defend herself against terror," says German Foreign Minister, endorses Op Sindoor
 World
World





